Telegram has become one of the most popular messaging apps in the world, boasting millions of users thanks to its unique features and strong focus on privacy. In our fast-paced digital landscape, individuals and organizations alike are seeking secure communication channels, and Telegram offers an appealing solution. With end-to-end encryption, self-destructing messages, and secret chats,
Originally launched in 2013 by Nikolai and Pavel Durov, Telegram set out to create a more secure messaging service. Its popularity grew from its ability to combine user-friendliness with cutting-edge security protocols. Users can share various types of content, from text messages to multimedia files, all while keeping their conversations private. However, the app is not without its flaws or vulnerabilities, making it crucial for users to stay informed about best practices in security, especially for sensitive communications.
Why Focus on Ethical Hacking?
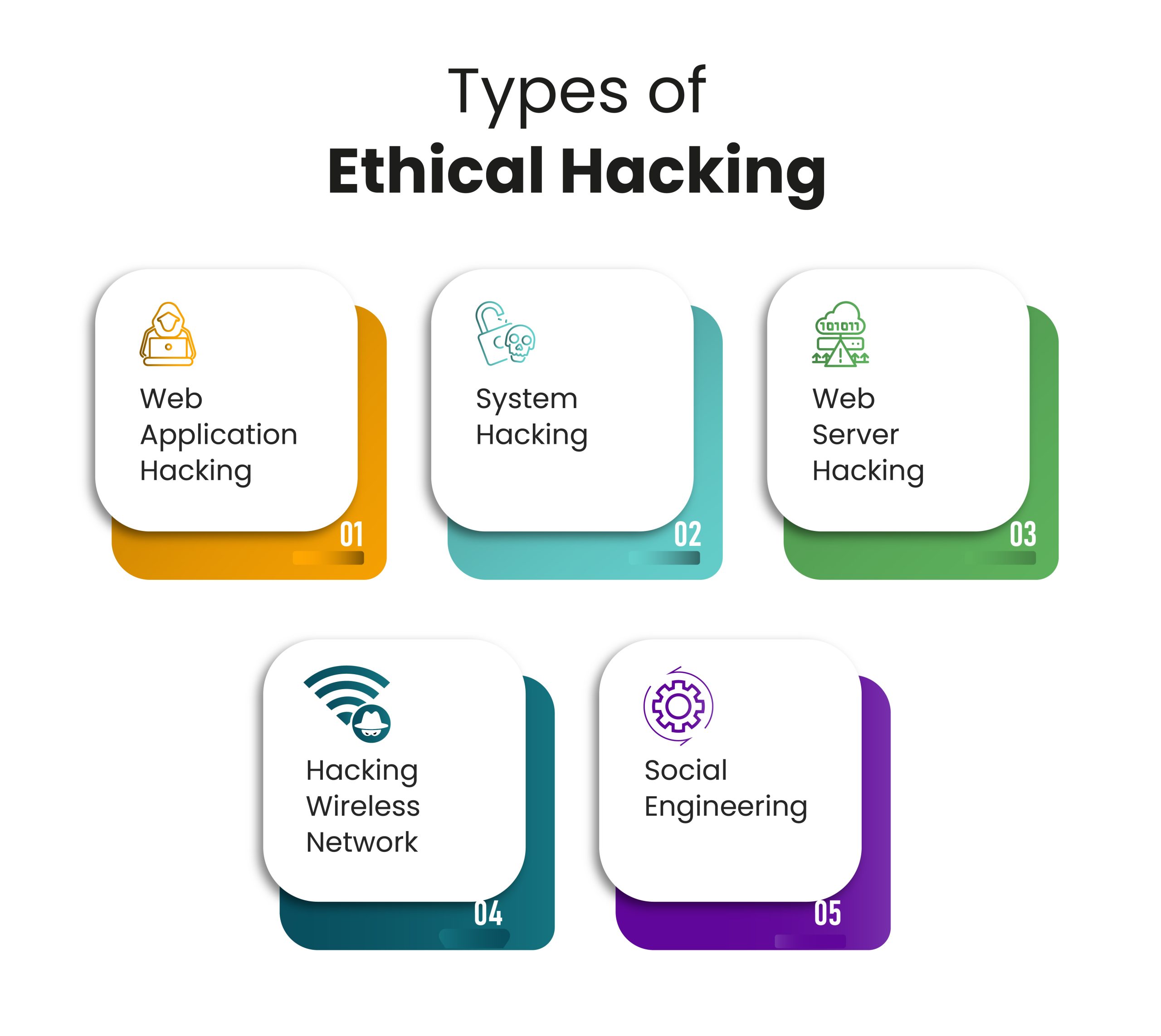
When we think about hacking, it often conjures up images of crackdowns and cyber crime. However, there's a gallant side to this world known as ethical hacking. But what exactly does that mean, and why should we focus on it when discussing platforms like Telegram? Let's break it down.
1. Understanding Ethical Hacking: Ethical hacking involves using the same techniques and tools that malicious hackers use but with the permission of the organization or individual whose system is being tested. The goal? To identify vulnerabilities before they can be exploited by those with bad intentions.
2. Protecting User Data: In a world increasingly relying on digital communication, user data is more vulnerable than ever. By focusing on ethical hacking, we can better protect user data, ensuring that personal conversations remain just that—personal!
3. Strengthening Security Protocols: Ethical hackers can help develop stronger security measures for apps like Telegram. They provide valuable insights into potential weaknesses, allowing developers to enhance encryption protocols and other security features.
4. Building Trust: Companies that invest in ethical hacking can foster trust with their users. Demonstrating a commitment to security sends a clear message that user privacy is a priority.
In conclusion, focusing on ethical hacking is not just about combating cyber threats; it's about fostering a more secure and trustworthy digital landscape for users everywhere.
Common Security Features of Telegram

Telegram is often recognized as a secure messaging platform, and it boasts several features designed to protect user privacy and data. Understanding these features can help users navigate the app with a more informed mindset. Here are some of the key security elements:
- End-to-End Encryption: One of Telegram’s strongest features is its end-to-end encryption, which ensures that only the communicating users can read the messages. This feature is available in “Secret Chats,” making them a great option for those who want to keep their conversations private.
- Self-Destructing Messages: In Secret Chats, users can set a timer for messages to disappear after being read. This adds an extra layer of privacy, ensuring that sensitive information doesn’t linger longer than necessary.
- Cloud Storage: Telegram offers cloud-based storage that allows for easy backup and accessibility. While messages in the cloud are encrypted during transit, they are not end-to-end encrypted like those in Secret Chats, so users should be mindful of the information they share.
- Two-Factor Authentication (2FA): Users can enable 2FA in their account settings to add a second layer of security. This means even if someone obtains the user’s password, they won’t be able to access the account without the second factor, usually a code sent to the registered phone number.
- Active Sessions: Telegram allows users to review active sessions across devices and, if necessary, terminate any suspicious sessions. This feature is useful for maintaining control over account access.
These features collectively make Telegram a compelling choice for users concerned about security. However, it’s worthwhile to remain vigilant and practice good digital hygiene.
Ethical Hacking Techniques for Telegram
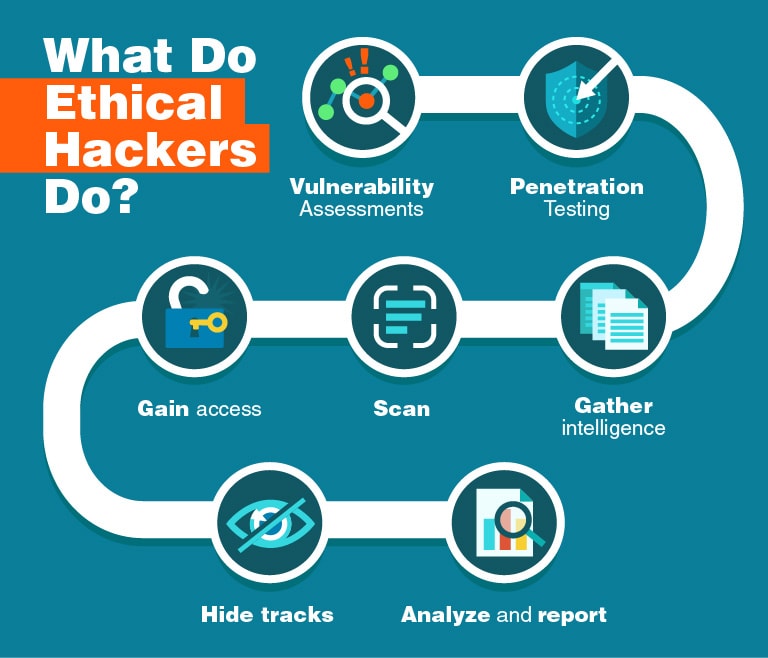
Ethical hacking involves employing techniques to identify vulnerabilities in systems and applications to enhance security. When it comes to Telegram, ethical hackers use various methods to test and evaluate the platform’s security. Here are some common techniques:
- Penetration Testing: This involves simulating attacks on Telegram’s infrastructure to identify potential vulnerabilities. Ethical hackers attempt to exploit weaknesses, helping developers patch them before malicious hackers can take advantage.
- Social Engineering: Ethical hackers analyze how susceptible Telegram users might be to social engineering attacks. This includes phishing attempts where attackers impersonate legitimate entities to trick users into sharing their login details.
- Traffic Analysis: By examining network traffic, ethical hackers can assess the data being transmitted between users and Telegram’s servers. They look for unencrypted data and any other security flaws that could be exploited.
- Bug Bounty Programs: Telegram runs bug bounty programs that encourage ethical hackers to find and report security vulnerabilities. These programs often offer financial incentives, helping improve the app's security infrastructure.
- Code Review: If ethical hackers have access to Telegram's source code, they can conduct comprehensive reviews to detect security lapses, helping ensure robustness against potential threats.
Using these ethical hacking techniques allows both users and developers to better understand the security dynamics of Telegram, ensuring a safer environment for communication.
Potential Vulnerabilities in Telegram
When discussing the security of any messaging app, it’s essential to address potential vulnerabilities. Despite Telegram’s robust encryption and security measures, no platform is entirely immune to risks. Understanding these vulnerabilities can help users stay better protected.
- End-to-End Encryption is Optional: Unlike some apps that provide end-to-end encryption for all chats, Telegram offers it only in "Secret Chats." Regular chats are encrypted between the client and server but may not have the same level of protection.
- Cloud-Based Storage: Telegram stores messages on its servers, which can be a double-edged sword. While this allows for seamless access across devices, it can also present a risk if server security is compromised.
- Phone Number Dependency: Telegram requires users to register with a phone number. This makes it easier to find and connect with others but could also expose users to targeted harassment or tracking.
- Bot Vulnerabilities: Telegram Bots can be incredibly useful, but they can also be a point of exploitation. Poorly designed bots may expose users to malicious links or hackers who could intercept data.
- Third-Party Apps: Many users access Telegram through unofficial third-party applications. These apps may not uphold the same security standards, potentially putting user data at risk.
By understanding these vulnerabilities, users can make informed choices about their communication habits on Telegram, fostering a more secure environment.
Best Security Practices for Users
When it comes to online communication, it’s always better to be safe than sorry. Here are some top-notch security practices that every Telegram user should consider incorporating into their routine:
- Use Secret Chats: Whenever possible, opt for Secret Chats, which offer end-to-end encryption. This ensures that your messages can only be read by the intended recipient.
- Enable Two-Step Verification: Protect your account by enabling two-step verification. This adds an extra layer of security by requiring a password beyond just your phone number.
- Be Cautious with Links: Always be wary of clicking links received from unknown contacts. Phishing scams are rampant, and it’s vital to verify the sender before opening anything.
- Regularly Update Your App: Keep your Telegram app updated to the latest version. Updates often contain security patches and enhancements that protect against emerging threats.
- Avoid Unofficial Clients: Stick to the official Telegram app to minimize risks. Unofficial or modified versions may have vulnerabilities or malicious code embedded.
- Limit Group Membership: Be selective about joining groups. Some groups may share malicious content, so it’s crucial to know who you're interacting with.
By following these best practices, users can significantly enhance their security on Telegram, ensuring that their communications remain as private and protected as possible.
Understanding Telegram Security and Ethical Hacking Techniques
Telegram has gained immense popularity as a messaging platform due to its unique features such as end-to-end encryption, self-destructing messages, and secret chats. However, understanding its security mechanisms and the potential vulnerabilities is crucial for users who prioritize their safety and privacy.
Telegram uses a proprietary encryption protocol called MTProto. This encryption helps to secure chats, making it difficult for third parties to eavesdrop. Nevertheless, there are techniques employed by ethical hackers to identify vulnerabilities in the system, which can unfortunately be misused by malicious actors. Here are some key security aspects to consider:
- End-to-End Encryption: Only the sender and receiver can read the messages in secret chats.
- Two-Factor Authentication: Adds an additional layer of security to user accounts.
- Cloud-Based Storage: Allows access across devices, but poses risks of unauthorized access.
Despite these protections, Telegram users must remain vigilant. Ethical hacking techniques often focus on:
| Techniques | Purpose |
|---|---|
| Phishing | Tricking users into providing account credentials. |
| Man-in-the-Middle (MitM) Attacks | Intercepting communications between users. |
| Social Engineering | Manipulating users into divulging confidential information. |
In conclusion, while Telegram provides robust security features, understanding how they work and being aware of potential vulnerabilities is essential for users. By employing best practices such as two-factor authentication and staying cautious of suspicious links or contacts, users can significantly enhance their security on the platform.