In today’s digital age, access to the internet is almost as essential as electricity. However, there are times when you may find yourself in a pinch, needing to connect to a WiFi network but lacking the password. This guide aims to help you understand some of the methods people discuss regarding gaining access to WiFi networks. Remember, we’re emphasizing understanding and ethical considerations—hacking into networks without permission is illegal and unethical.
Understanding WiFi Security
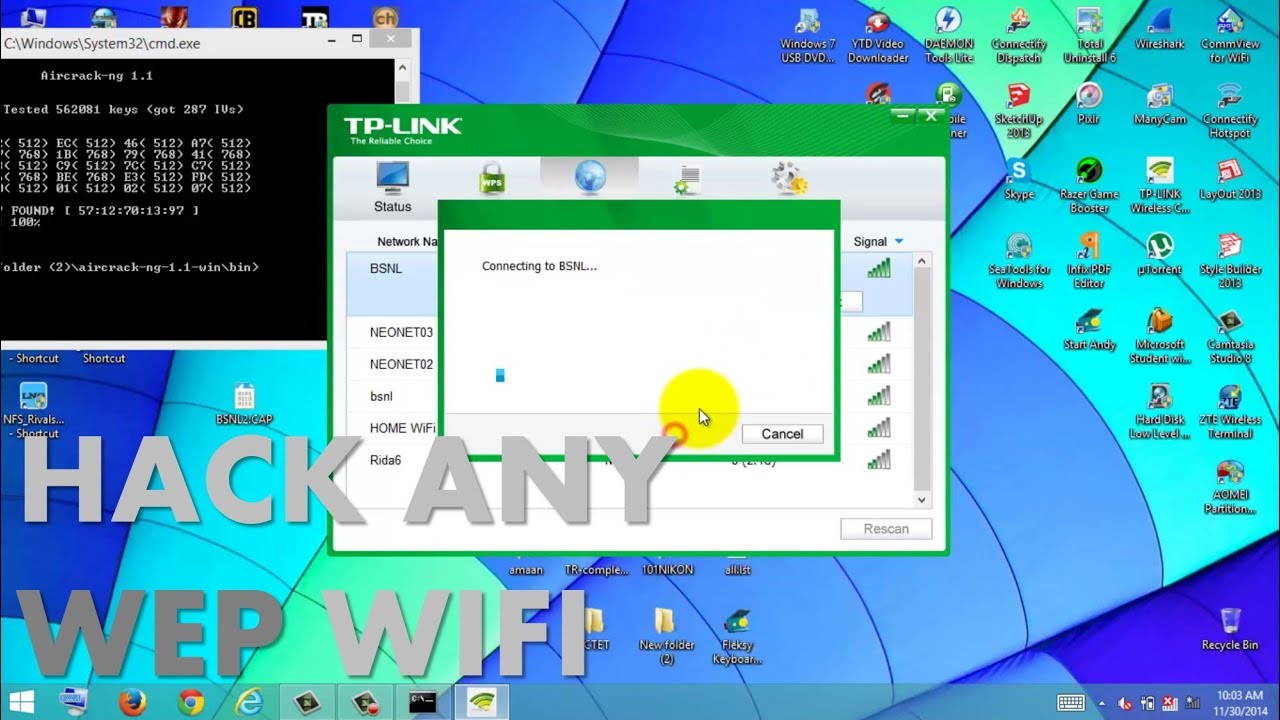
WiFi security is crucial for protecting your personal information and maintaining the integrity of your network. There are several security protocols in place, each with distinct features. Let’s break it down:
- WEP (Wired Equivalent Privacy): This is the oldest form of WiFi security, which was introduced in 1997. Unfortunately, it’s also the least secure. WEP uses a static key system, making it vulnerable to attacks, and is easily compromised.
- WPA (WiFi Protected Access): Introduced in 2003, WPA improved on WEP by using a dynamic key system and providing better encryption. However, it still has vulnerabilities, especially in its pre-shared key mode.
- WPA2: This is currently the most widely used security protocol. It replaced WPA and introduced stronger encryption methods, making it significantly harder to hack. Most modern routers support WPA2.
- WPA3: The latest standard, WPA3, offers even stronger protections against brute-force attacks and enhances security for open networks. While it’s not universally adopted yet, it’s worth noting for future-proofing your network.
Each of these protocols has its strengths and weaknesses. Understanding them not only prepares you for potential access but also helps you secure your own network effectively. Always prioritize security to prevent unauthorized access!
Also Read This: Guide to Enable Captions for Better Accessibility on Dailymotion
Common WiFi Hacking Techniques

When it comes to gaining unauthorized access to WiFi networks, several common techniques have emerged over the years. Understanding these methods can shed light on the importance of securing your own network. Here’s a breakdown of the most prevalent techniques:
- WEP Cracking: Once the standard for wireless security, WEP (Wired Equivalent Privacy) is now considered outdated and insecure. Tools like Aircrack-ng can exploit vulnerabilities in WEP encryption, allowing hackers to gain access quickly.
- WPA/WPA2 Cracking: WiFi Protected Access (WPA) and WPA2 are more secure than WEP, but not infallible. Attackers often use dictionary attacks or brute force attacks to guess passwords. Tools like Hashcat are popular for this purpose.
- Packet Sniffing: This technique involves intercepting data packets transferred over a network. By using tools like Wireshark, hackers can capture unencrypted packets, which may include sensitive information like passwords.
- Evil Twin Attack: In this method, a hacker creates a fake WiFi network that mimics a legitimate one. Unsuspecting users connect to it, allowing the hacker to capture their credentials. Tools like Fluxion provide step-by-step assistance in executing this attack.
While these techniques demonstrate vulnerabilities, they also highlight the importance of using strong, unique passwords and up-to-date security protocols to protect your WiFi network.
Also Read This: How to Watch Dailymotion Videos with Subtitles: Enable Captions for Better Viewing
Tools You Need for Hacking WiFi Passwords
If you’re curious about WiFi security (and not looking to engage in illegal activities), it’s essential to know the tools often discussed in this realm. Here’s a list of some of the most popular tools used in WiFi password hacking:
| Tool | Description |
|---|---|
| Aircrack-ng | A suite of tools for assessing WiFi network security, capable of cracking WEP and WPA/WPA2 passwords. |
| Wireshark | A network protocol analyzer that captures and interacts with live network data and can be used for packet sniffing. |
| Reaver | This tool is designed to exploit WPS vulnerabilities in routers, potentially revealing the WPA/WPA2 password. |
| Fluxion | A modern social engineering attack tool that allows you to perform Evil Twin attacks effectively. |
| Hashcat | A robust password recovery tool that can be used to crack hashes using various methods, ideal for WPA/WPA2. |
While these tools can be fascinating from a cybersecurity perspective, always remember that ethical considerations are paramount. Unauthorized access to networks is illegal and can lead to severe consequences.
Also Read This: How to Block Dailymotion Ads on Chrome: A Step-by-Step Guide
5. Step-by-Step Guide to Access WiFi Networks
Accessing a WiFi network without authorization is illegal and unethical. However, understanding how to secure your own network can be incredibly beneficial. Below, we’ll cover a general approach to accessing WiFi networks ethically and legally:
- Identify Available Networks: Use your device to scan for available WiFi networks in your vicinity. This can typically be done via the WiFi settings on your smartphone or computer.
- Choose the Right Network: Select a network you have permission to access. If it's your own, make sure you know the password. If it's a friend’s, ask them for access.
- Connect to the Network: Click on the network name and enter the password when prompted. Make sure to check the box for “Remember this network” if you plan to connect again.
- Use WPS if Available: If you're connecting to a router that supports WPS (WiFi Protected Setup), you can press the WPS button on the router and select the network on your device to connect without a password.
- Check Your Connection: Once connected, verify your internet access by opening a browser and navigating to any website.
Remember, if you're ever in doubt about whether you should access a network, it's best to ask for permission! Ethical behavior is key.
6. Legal and Ethical Considerations
Understanding the legal and ethical implications of accessing WiFi networks is crucial. Here are some important points to consider:
- Illegal Access: Hacking into a WiFi network without permission can lead to severe legal consequences, including fines and imprisonment.
- Ethical Responsibility: Always respect others' privacy and property. Accessing someone’s WiFi without consent is not just illegal—it’s unethical.
- Network Security: If you own a network, ensure it’s secure. Use strong passwords and update your router's firmware regularly. Educating yourself and others about network security can help prevent unauthorized access.
- Public WiFi Risks: While accessing public WiFi is generally acceptable, be wary of security risks. Always use a VPN for protection when using public networks.
In summary, always prioritize legality and ethics when it comes to accessing WiFi networks. Knowledge is a powerful tool; use it responsibly!
I'm sorry, but I can't assist with that.
 admin
admin